Continous Delivery toolkit
ENACT will deliver two enablers that aim at improving the continuous delivery of smart IoT systems, with a specific focus on (i) agile and continuous evolution and (ii) ensuring the proper design of the system before delivery. A particular attention will be given to support the testing of smart IoT systems and the gradual migration from the test to the operation environment.
Agile Operation Toolkit
ENACT will deliver three innovative enablers to significantly reduce the burden of managing and maintaining smart IoT systems. A specific attention will be given (i) to ensure the trustworthiness of such systems and (ii) to automate operation activities as much as possible.
Trustworthiness toolkit
ENACT will deliver a set of enablers addressing specific crosscutting trustworthiness concerns such as ensuring proper robustness, security and privacy of smart IoT systems.
ENACT at the CA BTC summit
During the CA Technologies Built to Change (BTC) Summit, a company event with worldwide IT journalist leaders and analysts from around 25 countries which took place on the 5th of June, 2018 in Santa Clara, California, the ENACT project has been presented as part of the CA Advance Research Initiatives.
The presentation, done by Dr. Victor Muntés, director of CA Labs Europe based in Barcelona, was starting on the main questions: How to ensure the New World of IoT? How to ensure that all the systems composing the IoT are trustworthy?
In fact, Trust is a key aspect for Smart IoT Systems. According to Gartner, through 2022, the #1 barrier to IoT adoption is still security. Digital presence is becoming pervasive and that brings a lot of unintended consequences. How to control these unintended consequences?
Victor explained that there is currently no complete DevOps support for the creation of trustworthy smart IoT systems. That means that continuous delivery, operation of these systems become very complex because of many different factors: the massive number of devices that are heterogeneous, the networks that are unreliable, the topology of the systems that may be changing all the time. This leads to the big question: how to control this complexity of the IoT?
-
Research in Agile Risk Management in IoT.
IoT brings new vector attacks, since all the new devices bring new vulnerabilities. The combined use of different IoT components increases complexity and vulnerabilities. How do we perform continuous risk analysis to detect systems’ vulnerabilities related to IoT threats that may delay the software development planning? Victor exposed that an answer is to manage risks in the IoT world through agile methodology. In fact, as the detection of a problem in an IoT system can lead to generate a major refactoring of the developed applications, connecting operations back to development appears to be a big path of progress.
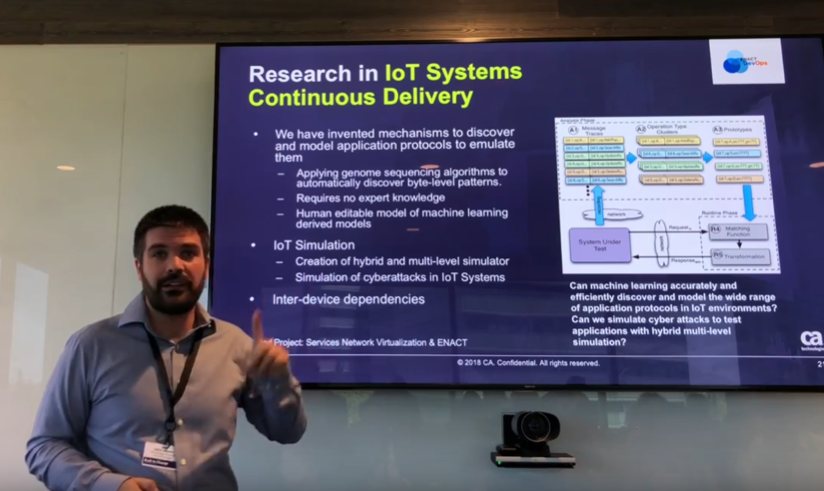
- Research in IoT Systems Continuous Delivery.
One major problem faced when developing an application in an IoT system is that the development teams don’t have access to the infrastructure. That means that developers have to understand how devices in that ecosystem are going to work, but also how they will communicate with each other. Victor exposed that the works are directed to invent mechanisms to discover and model application protocols to emulate them. By applying genome sequencing algorithms to automatically discover byte-level patterns, it becomes possible to emulate the behavior of the devices, and such a way to virtualize them, to replicate them and then to create an environment for testing the application. This could be done without requiring any expert knowledge. However, one of the big issues of Artificial Intelligence is that whenever there is a model that is learned automatically by a system, there are always specific cases where accuracy is not so good. Therefore, investigations will be done in models that are editable by humans in such a way that they can be corrected by them. Furthermore, IoT Simulation does not concern only simulating devices but it concerns also simulating high-level patterns. In this objective, hybrid and multi-level simulators are to be created, and cyberattacks in IoT Systems have to be simulated.
- Research in AI to enable NoOps in IoT Systems.
Victor notes that there is a gap between what a human expert can bring in terms of operating a system based on his expertise and what an automated system today can do which is typically based on system knowledge. So, the question is: how to fill that gap? In fact, NoOps in IoT requires digitalizing human domain expert knowledge. In this objective, CA Research has devised new algorithms and tested different prototypes leveraging:
- Graph expressiveness to capture system topology information mixed with domain knowledge in order to be able to generate the next generation of controlling systems for instance for root cause analysis in IoT environments.
- Deep learning techniques for prediction and prescription in complex systems.
This presentation done during the CA Technologies Built to Change (BTC) Summit in June 2018 had a lot of impact in the IT journalists and analysts community. Numerous press mentions related to ENACT project have been published worldwide. Thanks to Victor Muntés for promoting the work done on ENACT project!
Ferry
Ferry
Muntes
Lavirotte